PlexiMail: The Counterseal PlexiMail Web3 Edition
Effective August 1, 2023 | Archived versions
General

The objective of PlexiMail is NOT to directly compete with messaging applications like Gmail, Outlook, Facebook, Twitter, WhatsApp, Signal, and others, which are public-facing and require the surrendering of your Personally Identifiable Information (PII) right from the beginning in signing up for an account. Instead, our purpose is to address a gap in online services by providing the means for all of us to engage in profoundly private communication. This is achieved in a manner that is permissionless, distributed, invisible, and leaves no trace – distinctly different from conventional options. It is part of an effort to build a logically separate but parallel universe, countering the prevailing surveillance capitalism. It, by design, allows anonymous participation without the need for sign-up in this alternate universe.
PlexiMail provides a specific solution for a particular set of issues. Naturally, it remains susceptible to various attacks inherent to the platform from which PlexiMail runs, including malware, side-channels, drive-by attacks, phishing, IP source tracing, location tracing, geofencing, IMEI and more. A straightforward "best practice" is to operate PlexiMail on a dedicated live Tails USB package through the Tor browser without enabling persistent storage and to boot the USB solely on a robust Wintel platform with a secure BIOS/UEFI. You can adjust your day-to-day PlexiMail practices and make practical trade-offs according to your own assessment of the attack surface based on your threat model.
Summary
Secure Mail is a loaded yet vague term. While its aim is clear – protecting privacy from unwanted surveillance – the methods to achieve this are uncertain. Over time, benchmarks like End-to-End encryption have become common. However, shielding metadata remains a challenge, despite earnest efforts. We believe our PlexiMail offering has successfully accomplished this challenging goal.
Engaging with the internet can at times resemble being seated on a symbolic conveyor belt, where one is metaphorically disrobed, left exposed and vulnerable to the impacts of diverse service providers through location tracking, search history, contact tracing, browsing history, biometric data, when you go to sleep and wake up, how often you recharge your battery – the list goes on and on. This unrelenting assault on our privacy will undoubtedly be exacerbated by the ominous rise of AI-assisted data collection. In this default mode of internet surfing, under the intensive surveillance cloud, service providers simply cannot be trusted. This recognition becomes particularly crucial when the focus turns to prioritizing metadata cloaking. We firmly assert that the current single-track architecture of the Internet, which intertwines private interactions with public ones on a shared network substrate, serves as a fundamental origin of the majority of the risks and complexities. This understanding drives our most important design choices, including employing a trustless approach, collecting no user Personally Identifiable Information (PII), refraining from storing any application contents, offering utility services that are not user-specific similar to public utilities (e.g., Tor switching and zero-knowledge delivery notification relay), and enabling anonymized blockchain smart contracts through Plexi digital cash tokens.

Prior to telecommunication advancements, privacy was a given. The proliferation of the Internet and mobile phones escalated data collection, paving the way for Surveillance Capitalism. This led to a marketplace of service providers engaging in data-driven surveillance, ultimately forming a global network where personal information became a commodity, transforming the landscape of personal privacy. Now, we've come full circle. Built upon the PlexiMail architecture, we can once again restore the natural setting for private and invisible social interaction, amidst the looming backdrop of a blockchain smart contract and Web3Storage structured as utility services, with only the faceless delivery notifications being passed around. The bulk of the cost is carried by individual users for their Web3Storage subscription, which is free if subscribing to less than 5GB. This also demonstrates the cost advantages of a true distributed service infrastructure that inherently repels surveillance.
These design decisions prioritize privacy, ensuring warrant-proofness by design, and enhancing security. Architecturally, they establish two parallel universes—one for public interactions with anticipated surveillance and another for private exchanges, free from unwarranted scrutiny. This is made possible by decentralized identifiers (DIDs) secured through a blockchain-based smart contract, and tokenized Web3 storage that grants each user their individual email repository. This offering demonstrates that with a small effort, we can all be self-sufficient, taking charge of our own destiny in terms of both data and metadata privacy.
There is significant potential to delve into and uncover the successful yet unconventional email approach we offer. While the initial setup may be somewhat intricate due to the inherent costs of self-reliance, we are confident that your patience will be generously rewarded.
Email as Our First Web3 Release
Many individuals have multiple email addresses, each containing Personally Identifiable Information (PII), leaving digital breadcrumbs everywhere and making them highly vulnerable to phishing and spam attacks. The provision of free email services often comes at the cost of our privacy, as we become the product, aligning with the primary objective of such services.
PlexiMail leads the charge in liberating users from the shackles of compromising arrangements with mainstream email providers. By tokenizing and democratizing the critical resources of storage and network delivery services, it offers a solution where individuals can reclaim control over their emails and contacts, free from the need to engage in Faustian bargains. This groundbreaking approach, facilitated by the Web3 revolution, ensures a fair and decentralized distribution of resources, empowering users to shape their digital communication experiences on their own terms, without sacrificing their privacy or security.
PlexiMail revolutionizes email messaging by completely reimagining its architecture and eliminating the traditional role of email providers. In essence, it empowers users to redefine their private identities and maintain non-public-facing personas by adopting independent blockchain addresses for each of their roles. Through the Trust On First Use (TOFU) protocol, individuals can personally construct their private social circles while safeguarding their contact information using the PlexiMail Smart Contract on the blockchain. Embracing this self-managed paradigm, PlexiMail has successfully reinvented the wheel, prioritizing privacy by cloaking all metadata.
Differentiation
Although PlexiMail may resemble an email platform, it operates as a distinct entity with the purpose of carving out a private space within the internet. This realm is currently dominated by Surveillance Capitalism, which suffocates its users. The emergence of blockchain technology and the Web3 revolution brings hope and inspiration. However, before immersing ourselves in this latest gold rush, we must carefully reassess our needs and requirements. It is crucial to adopt these new technologies thoughtfully and avoid squandering the opportunities they offer, especially when it comes to privacy. Blockchain provides an immutable public ledger, with "public" being the operative word. Harnessing its immutability while managing the inherent risk of public exposure requires deliberate effort to create privacy-centric applications. We must also resist the temptation to view cryptocurrencies solely as a printing press for money. Designing blockchain solutions based solely on their popular appeal would only reinforce the misconception that "Cryptocurrencies have no intrinsic value." On the other hand, some projects have taken an extreme approach by completely eschewing cloud resources in the pursuit of privacy (e.g., Briar). Those approaches risk foregoing the significant technological advancements available.
The following is a reprint from a FBI training manual reported in The Record article:

As a self-proclaimed Web3 application, we differentiate ourselves from other trending products based on our design goals, aversion to service providers, selection of software delivery platform, and certain design choices that take advantage of cloud resources securely and anonymously. Right from the start, as no personally identifiable information (PII) is collected or required by PlexiMail, there is no possibility of any leakage that could be attributed to any individual. Users are identified through their PlexiMail addresses, which do not directly lead to individual users. To put it differently, if PlexiMail were to become a subject of interest for the FBI, they would simply have to put "Nadda" under the PlexiMail column in the training manual. Even if the identity of the individual behind a PlexiMail address is pierced, in order to uncover anything meaningful, the FBI would still need to locate, decrypt, and unlock their private session cryptons. These cryptons can possess a decryption entropy even stronger than that of a typical blockchain account address and do not reside within any PlexiMail utility services (refer to point 4 below).
Specifically,
No Personally Identifiable Information (PII) required, with social circles constructed only based on Trust On First Use (TOFU) protocol.
No shared storage or servers: PlexiMail utilizes self-managed and tokenized Web3Storage, eliminating the need for external shared Service Nodes (such as IM Session) for message storage and removing the size limits on the content, as long as the Web3Storage subscription covers it. This self-sufficiency empowers individual users and naturally provides self-managed backup and restore functions. Most importantly, relying on shared resources exposes a significant attack surface. The unstoppable rise of AI would undoubtedly exploit this vulnerability, rendering the effectiveness of all manual penetration tests outdated. The only truly effective solution is to drastically reduce all shared exposures and architecturally distribute risks to anonymized individual users, leveraging their large numbers. Incidentally, this architecture significantly reduces the effectiveness of any unwanted surveillance measures as well.
Traceless implementation: PlexiMail content is not stored in any shared service storage, ensuring no digital exhaust leakage when not in use. The browser is simply used as a software delivery vehicle to populate the browser sandbox with PlexiMail client logic during a session. When not running, it leaves no traces on the browser, enabling complete bootability from a Live Tails USB stick. This makes it impossible to determine if an individual is a PlexiMail user, even when their devices are confiscated.
Crypton: PlexiMail runtime session contexts are encapsulated through a cloud-based software construct called Crypton. Crypton is stored in the users' private Web3Storage fully encrypted and doubly locked with cryptographic keys of greater strength than any of the blockchain account addresses. Using Cryptons, users can adopt multiple PlexiMail identities, each tailored to their specific private circles and applications. This functionality is similar to a cryptocurrency wallet that manages multiple blockchain accounts for various financial purposes.
Server-less/Provider-less Architecture: PlexiMail distributes almost all functions to the browser-based fat client, utilizing a smart contract on the blockchain for application-specific session services. These session services are further supported by a utility service for message notification. Within this context, the utility service is designed to provide a set of dedicated functions without any knowledge of individuals who are requesting from the upper layer.
Tor support: PlexiMail leverages the browser platform to seamlessly integrate with the generic, dedicated, and single-purpose Tor network. This network boasts ten times more nodes than Oxen service nodes and is considerably simpler. As an email application, PlexiMail is immune to end-to-end traffic analysis, which is considered the top threat to the Tor network.
Public Disclosure of Privately Negotiated Contracts: The architecture of PlexiMail is particularly well-suited for contract negotiations that require privacy, such as employment offers, Non-Disclosure Agreements (NDAs), mergers and acquisitions, industrial plant closures, outsourcing, out-of-court settlements, and more. The negotiation process through PlexiMail remains tightly sealed, but the final settlement necessitates certain procedures, including notarization, legally binding signature collection, contract registration, and archival. This is where PlexiMail truly excels: by blending with blockchain technology, it supports a high level of confidentiality and provides publicly provable evidentiary records when necessary.
Anonymous Blockchain Onboarding: Alongside the learning curve associated with blockchain technologies, purchasing cryptocurrencies can also be a complex process. This complexity becomes particularly frustrating when dealing with "micro" transactions involving only a few dollars, or even pennies and cents. For privacy-oriented crypto applications, the onboarding Know Your Customer (KYC) requirements and the public nature of the blockchain also pose significant privacy challenges. To address these concerns, PlexiMail offers an affiliated "Token Store" that allows our users to purchase Avalanche AVAX (or other coins) using their credit cards. These tokens can then be utilized anonymously as a form of digital cash at a later stage. This makes the 'follow the money' analytics ineffective for tracing our users' identities.
Supported Web Browsers
Currently PlexiMail Web3 Edition runs on any platforms where HTML5 is supported, such as Chrome browser, Edge, Brave, Firefox, Opera, Safari, DuckDuckGo Private Browser, Tor Browser and all Chromium-based custom browsers. Some users install the Brave browser, which is also Chromium based, specifically to take advantage of its built-in Tor. For enabling Tor and other optioins, the Brave tab or windows need to be opened according to the desired level of security. The Tor Browser is also supported, although the performance is slow, as expected.
Architecture
The PlexiMail ecosystem consists of the following elements:
A browser-based client: This is where all the critical functions reside, commonly described as a "fat" client. Each user is represented by a cryptographic key-pair, self-managed through a crypto wallet sepcifically designed for maintaining a user's identity through the fat client software represented by their PlexiMail Address. A user self-directs all thier PlexiMail operations through the wallet and the fat client, without relying on any third party email services. It is open sourced and auditable. Combined with a few utility services, it weaves together a truly permissionless and trustless email service for maximal metadata protection.
Smart Contracts: This implements a Registration Service, that allows a PlexiMail address to publish its contact information only after the applicant proves cryptographically their ownership of the associated private key. PlexiMail supports a number of blockchains so users can select one that matches their security requirement and cost considerations. They can even choose to register with multiple smart contracts to enhance their protection through redundancy. Currently the Ethereum-compatible Avalanche is the supported blockchains.
Web3Storage: This is the affordable service where the sender deposits their plexiMails before notifying the recipients. It is currently outsourced to https://web3.storage with all pleximails encrypted and packaged in IPFS format, based on tokenized cloud storage with universal accessibility and managed persistency. The service account is identified through traditional email address, which can be anonymized by adopting a burner address disassociated from all PII (Personally Identifiable Information).
PlexiMail Notifier: This is the service that notifies the PlexiMail recipients of any incoming mails or messages.
Both Web3Storage and Notifier are considered "Utility" services, as they perform a specific set of functions without having knowledge of the requesters' identities beyond their PlexiMail addresses. In the case of Web3Storage, only encrypted IPFS data are passed to the web3.storage service without revealing even the PlexiMail addresses or the PlexiMail application itself behind the service requests. Furthermore, as previously mentioned, we will be supporting a user registering over multiple smart contracts for enhanced protection through redundancy. Similarly, we will be offering similar redundancy support For Web3Storage and PlexiMail Notifier services through open API and sample open source server codes so our user communities can submit their own service implementations for approval.
Configuration Setup
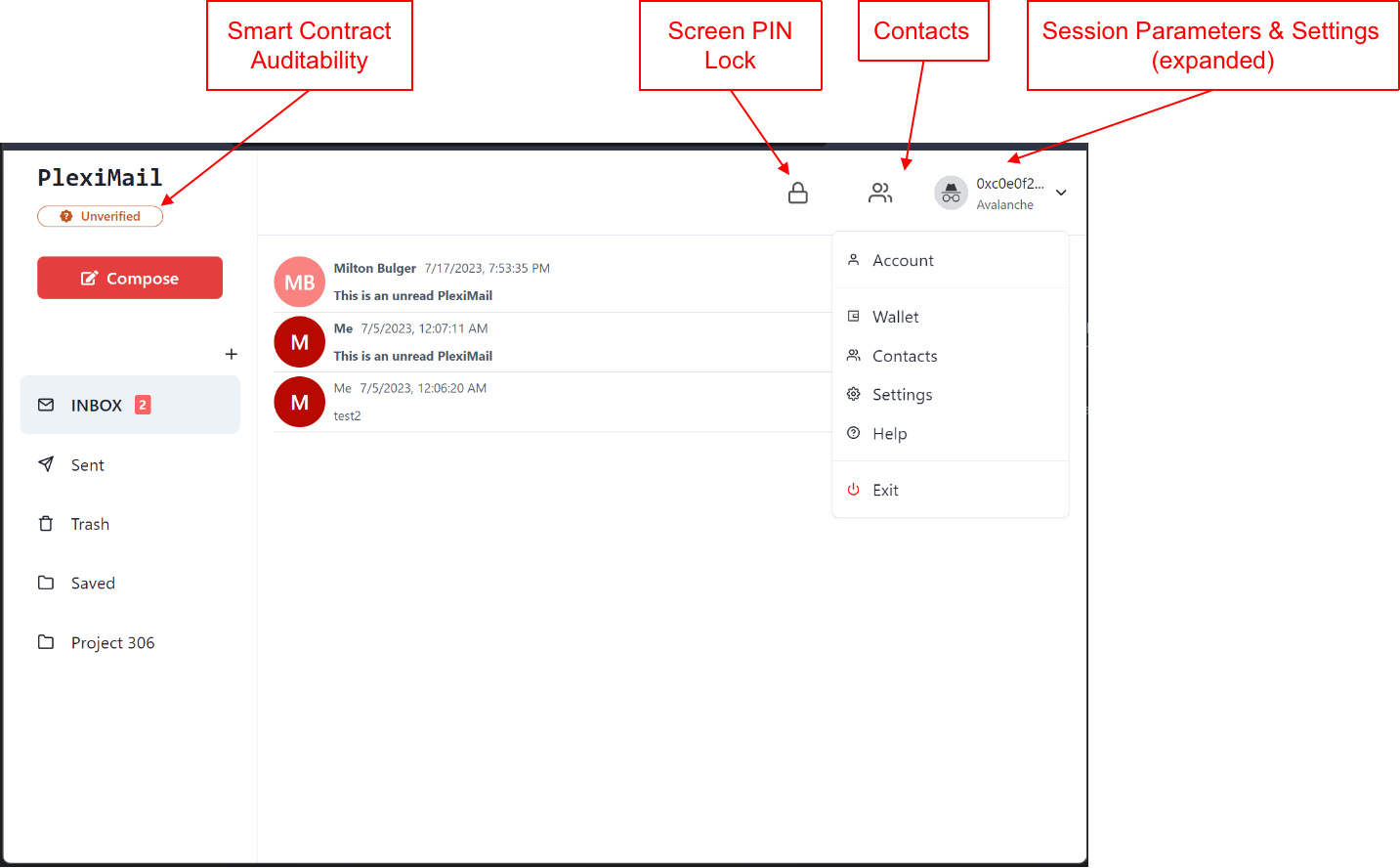
The above main PlexiMail operational screen is self-explanatory. However, before reaching this PlexiMail main screen, you need to provide the following parameters:
PlexiMail Address: Your PlexiMail addresses are created from your Avalanche accounts, jointly managed with a built-in crypto wallet or PlexiMail Wallet. Your PlexiMail Address can also be "published and registered" with the PlexiMail infrastructure by executing a smart contract built into the Avalanche blockchain or other supported blockchains.
Private Web3 Storage: To get the free Web3 cloud storage, go to https://web3.storage. It relies on one of your public email accounts to authenticate you. The granted free Web3 storage is identified by its "API Token". Locate it in the Web3Storage dashboard under "Account". We also provide a new and simpler Web3Storage Beta feature: W3:UP. You can find more details about both the API Token and W3:UP options in the dedicated section Web3 Storage.
The above two steps involve some external applications we choose to work with. Please note that the wallet service and external web3.storage service are considered "utility services," and your publicly exposed emails there is in no way linked to your PlexiMail Address. Once they are installed, go into PlexiMail at https://ai-fi.cc and answer the in-program questions regarding those two established external applications.
There are two more steps remaining in the PlexiMail configuration:
Signal Runtime: This is the step for preparing the end-to-end encryption sessions based on the Signal Protocol. It uses the PlexiMail Address set up in Step1 as input to the PlexiMail smart contract for establishing the owner identity of the address.
PlexiMail Configuration: After the successful completion of all steps above, PlexiMail creates a Configuration file to record what has been entered. You will be asked to "Export" this file to a safe location, which would be required on a recovery run. If you lose this Configuration file, all your accumulated PlexiMail mails or correspondence would be rendered unreadable.
PlexiMail Running Sessions
To minimize the trackability of PlexiMail and maximize its tracelessness property, PlexiMail primarily utilizes the web browser as the software delivery vehicle fortified by code signature and versioning, refraining from implementing a dedicated app. Remaining true to its commitment to tracelessness, there is no indication that a user has engaged with PlexiMail once they exit the browser tab running the application. All PlexiMail session data, communication history, and identity keys are securely stored in users' private cloud (Web3Storage) using a doubly-locked software apparatus known as Counterseal Crypton.. PlexiMail does not use iCloud or Google Drive in its operation, except the keychains when configured by the users for maintaining a local cache until "exit".
Quoting Bruce Schneier, "The whole notion of passwords is based on an oxymoron. Unfortunately, if it's easy to remember, it’s something non-random like 'Susan'. And if it’s random, like 'r7U2*Qnp,' then it’s not easy to remember." This is indeed the case where the password is the only thing separating you from your secrets. The surprisingly straightforward solution to break this conundrum is to introduce an additional mechanism that does not require remembering, relying on the power of redundancy to enhance the utility of a lone password. This is how the apparatus of Crypton came about.

Users create a PlexiMail session by first visiting https://mail.ai-fi.cc and defining its runtime environment through the configuration wizard. A successful configuration effort produces a configuration database, each identified through its unique wallet, which is then stored in their privately owned Web3Storage. This database is doubly locked through the "Crypton" apparatus, employing two lock mechanisms as conceptualized in the diagram above, which require two independent secrets to unlock: the Passphrase and the Entropy Extender. Both secrets can have flexible entropy or "temperature," with the Passphrase intended to be memorized while the Entropy Extender is written down and securely stored. The presence of both the Passphrase and the Entropy Extender adds redundancy, ensuring that both elements are required to unlock a protected object. When combined, a Crypton can have greater cryptographic strength than any of the blockchain account addresses, as the Entropy Extender allows for arbitrary length. Operationally, a session and its progression or reincarnations can be pretty much identified and maintained through its associated Crypton. Its protection mechanism is similar to how an NFT is protected with a combination of blockchain and offchain immutable data but remains anonymous and not viewable by passersby. They are hidden in plain sight in the cloud, extending our private reach beyond physical limits. A common practice in efficiently managing multiple Cryptons is to use a single or similar Passphrase while assigning each Crypton a unique and distinct Entropy Extender.
A running session may be temporarily suspended and resumed by entering the PIN code; or signed out completely to terminate the session with all cached data cleared until the next round of activation, which offers the option of "Resume" to recover the previous session or "Start Over" to only inherit the wallet in order to start a brand new session. The "Start Over" would erase all your past emails in the previous sessions. Signing in from a different device would automatically force a sign-out from any outstanding session on other devices. Any signing in gives the opportunity to reset the PIN code.
Architecturally, all pleximails are stored in the senders' Web3Storage in IPFS format, locked away by keys mutually negotiated between the sender and individual recipients, and retrievable only by the original owners of the keys. The permanency of all the emails are guaranteed by Web3Storage/Filecoin and users' session Cryptons are the only pathways for retrieving them. Each user may create multiple session databases protected by their respective Crypton. Your Cryptons are permanent as long as you are in possession of their Passphrase and Entropy Entender. The traditional backup and restoral functions are neither needed nor provided, as all past emails are retrievable as long as one owns the keys of their encapsulating Crypton. This architecture also allows a user to relocate their Web3Storage to a different destination when there is a need to change their Web3Storage subscription for expansion or migration reasons. Check the "Settings" to locate this relocation function. With Cryptons, users can maintain multiple PlexiMail identities, each tailored to their specific private circles and applications, similar to a cryptocurrency wallet that manages multiple blockchain accounts for various financial purposes.
Risk Exposure and Live USB Stick
The protection of Cryptons for the configuration database can be made cryptographically stronger than any blockchain accounts by expanding their entropy. They are exposed to potential external risk only during their activation on specific browser platforms, which is considered well protected by modern day browser sandboxes. Users are strongly suggested not to install any third-party non-Ai-Fi extensions that may interact with PlexiMail. It is also a good practice to exit or sign-out the PlexiMail session if a user needs to idle the session for any significant period of time. Once you exit the PlexiMail session, your engagement or interaction through PlexiMail becomes nondiscoverable, leaving no trace behind.

Other possible PII leakages, such as the IP addresses or the geographical location of the involved parties, need to be defended individually. The most popular protection is the adoption of Tor, which is built in and may be enabled straightforwardly in many browsers such as Brave. A frequently adopted defense by PlexiMail practitioners is to produce a "Live" Linux on a USB stick based on a privacy-centric Linux distribution such as Tails. Since PlexiMail is browser-based, it is straightforward to implement a dedicated Tails specifically to run PlexiMail on a Wintel hardware. Since your PlexiMail runtime relies only on its configuration Crypton, this portable and stateless USB stick reduces your "attack surface" to the hardware and BIOS if configured wisely. Please visit https://tails.boum.org and review a step by step guide for full details. You can also convert your personally owned Windows desktop or laptop into a dual-boot platform, eliminating the requirement to carry your Talis USB stick when your Windows system is conveniently at hand by following similar steps outlined for Kali in the video: How to Dual Boot Kali Linux and Windows (in 10 minutes).
(Notes 7/2023: There seem to be some issues with the latest version of balenaEtcher when flashing the img of Tails to the USB drive. We resorted to Win32DiskImager for a part of this task and it worked after cleaning up all old partitions on the USB before flashing it.)
Crypto Wallet
Under PlexiMail, each user is represented by one or many Ethereum/Avalanche blockchain addresses. They are inherently "Burner Addresses" and may be discarded after specific use. They are not designed to be friendly or easy to use and are the opposites of those traditional identities-carrying PII (Personally Identifiable Information). You can make them less cumbersome by collecting and naming individual entries in the Contacts List. The tie-in of those unwieldy PlexiMail addresses/identities to their corresponding PII in the Contacts is strictly "local" or "private" to the trusted social circle privy to the exchanged content. Our users' contact list is hence local/private as well, created merely to ease the data entry for the communicating clients. To enter into a PlexiMail social circle, you need to be formally recognized and trusted/permitted through the manual and personal TOFU (Trust on First Use) process on a one-to-one basis. Make sure the exchange of TOFU messages is carried out out-of-band and confidentially, certainly not through the PlexiMail itself. When first contacting a specific person, we suggest using a convenient yet stringent mechanism for sharing those lengthy blockchain addresses.
Note that the PlexiMail address format takes after the traditional email and is presented as:

This is only displayed under the Settings-->Profile button in the upper right control panel of the ai-fi.cc webpages after the setup is successfully completed.
Your PlexiMail addresses are maintained in their respective Avalanche crypto wallet. PlexiMail maintains a built-in wallet, emphasizing the identity management and not the crypto transactions. Each instance of your PlexiMail session has its own wallet, containing a single PlexiMail address/identity encapsulated in a specific Crypton. With the Avalanche addresses as your email accounts/identities and the built-in wallet on your chosen platforms, your identities are automatically protected by 2 separate factors: the private keys embedded in your platform where the PlexiMail wallet runs on and the PIN code for protecting your cached PlexiMail session. It will be further strengthened when we integrate PlexiMail with our own custom PlexiWallet in the follow-on releases.
Some of our users request for the integration of the MetaMask wallet, which has been around for a while and survived many trials and tribulations and is considered reliable for our application. We don't expect our users to use their PlexiMail addresses for making crypto transactions, which inevitably leak PII. Contact our support if you have a special need for MetaMask.
To pay for running the PlexiMail Smart Contract, you need to run MetaMask with your PlexiMail address key-pair, which works in most of our supported browsers as an "extension" and can be easily enabled or installed. If you are not familiar with the concept of Crypto Wallet, or Smart Contract, or Blockchain in general, please try to install MetaMask carefully and follow their introduction of blockchain concept, which is very approachable. This is the minimum you have to pay for living off the grid of Surveillance Capitalism.
For average users, learning and running an external wallet such as MetaMask in order to fund their registration through the PlexiMail Smart Contract may pose a hurdle. Running a private crypto wallet and keeping it anonymous is also not straightforward, let alone the startup cost of creating an external crypto wallet with any crypto exchanges. This difficulty is particularly aggravated by the fact that the PlexiMail Smart Contract on the Avalanche blockchain incurs only a "micropayment" of less than $1. Setting up a private account with a crypto exchange is definitely an overkill. To overcome this difficulty, we provide a custom Plexi Token Service specifically designed for PlexiMail users.
Email Bridging
Due to its radically different architecture, PlexiMail is not interoperable with traditional email services. In other words, the traditional "federation" property has been designed out of PlexiMail. Crossing between PlexiMail and traditional email services requires a software "bridge" that is allocated limited network resources. Therefore, the application of bridging must be disciplined and is likely of limited utility since bridging PlexiMail to a traditional email address immediately leaks metadata and exposes PlexiMail to tracking and surveillance, even when conducted through VPN or Tor. A suggestion is to designate a PlexiMail address specifically for this purpose, without ever being involved in any other social entanglement, in order to avoid leaking any potential Personally Identifiable Information (PII).
When sending a traditional email through the PlexiMail bridge, all recipients must be of the same type—either all PlexiMail recipients or all requiring passage through the bridge. The bridging function is one-way and accepts no replies.
Web3 Storage
Currently Filecoin offers 5 GB of free cloud disk storage for each user interested in Web3 storage solutions which PlexiMail is built on. Before we make our UI more friendly, you need to go to https://web3.storage/account outside our website to apply for your private storage. Enter your personal email and follow the instructions (and ignore the Github option for now). Filecoin offers a well-designed frictionless onboarding process. Just need to locate where that "API Token", the identifier of your private storage, is and cut-and-paste it onto the PlexiMail configuration process according to our onscreen instructions.
The Web3Storage is well supported and you can find the answer for any of your questions at their website. Recently we also added support for the latest of the Web3Storage interfaces called W3:UP that only require your personal email for authentication from within our PlexiMail app without the need for your to locate the "API Token". W3:UP is still in Beta and therefore only available when you run on an Ethereum testnet. For the Ethereum/Avalanche Mainnet, you must configure the Web3Storage through the API Token.
All the PlexiMail content you send is stored in your own Web3 storage. The recipient will retrieve the received email from the sender's own private storage. Although it is in plain sight, it is virtually anonymous and fully encrypted through dynamic keys from your own wallets with strength equivalent to any public blockchain transaction keys. No one in the world, including Gmail, outlook, protonmail, to just name a few, knows anything ever existed about this correspondence between you and your intended recipients. This is how the PlexiMail metadata is protected. We certainly don't need to go to Switzerland for "Swiss Privacy", as PlexiMail is provably warrant-proof, as there is simply nothing we retain like those service providers for any institutions to issue warrants against.
Web3Storage grows out of the same tree as the NFT offline storage support. They are inherently "publications" of stored content meant for stable and long term references in IPFS format. For short-term transient data storage it is not a perfect fit. Currently the deletion of stored raw data is promised but not yet implemented by Web3Storage. This is expected to change in later releases. However, considering the inherent nature of emails designed for interpersonal communication, it is unrealistic to expect individuals to have absolute control over the fate of the emails they send. This observation renders the deletion concerns irrelevant. Instead, it becomes crucial to safeguard these emails through robust viewing authorization rather than tightly controlling their ultimate disposition. Another immediate win is that there is no longer a limit on how large the data we ship around (practically) can be, including all the attachments. The term of your Web3Storage subscription determines the allowed size of your pleximail, which can be made arbitrarily large.
See the Release Notes in a later section for discussion on some performance issues.
As always, YouTube is your best friend in learning Blockchain, Cryptocurrencies, Avalanche, AVAX, faucet, Ethereum, Sepolia testnet, MetaMask wallet, Web3Storage, Filecoin, etc.
Hiding in Plain Sight
The shared services in PlexiMail are purposefully architected to avoid any references involving users' personally identifiable information (PII). For example, while your private storage does indeed reside within the "cloud" thanks to our collaboration with Web3.Storage, there is absolutely no possibility of Web3.Storage tracing back to our users' PlexiMail addresses.
However, we surpass mere integration: we conceptualize this fusion as a "utility service" to ensure that it is completely devoid of any user-level information. It models after the 'Public Utilities' like public electricity and water supply, which are net/application neutral. This approach stands in stark contrast to conventional services operating under Surveillance Capitalism, which mainly concentrate on collecting information tied to your personally identifiable information (PII). This concept also enables us to open up our utility services, such as PlexiMail Notifier/Forwarder and private cloud storage, for open participation. Any user community can request PlexiMail to establish their own private instances of utility services.
This unique approach is further bolstered by the "stateless" design, encapsulating all state variables within a Crypton. This design ensures both the portability and device independence of your data within PlexiMail's ecosystem. It empowers us to function on diverse web browsers across a plethora of platforms, including the highly secure Live Tails Linux, which is endorsed as the most secure Linux by Edward Snowden. Get more details in the write-up The Ai-Fi Incognito Cloud.
Multiple Identities
Depending on your intended PlexiMail applications, the upper limit of 5 GB of free storage may be an issue for you. You can always upgrade it to the next paid tier of 30 GB or even higher. Note that the Web3Storage configured into an individual identity, represented by its identity wallet encapsulated in its respective Crypton, does not need to be fixed. A Web3Storage subscription may be shared among mulitiple identites and can switch around along the session axis as long as the user is given the access right.
However, the recommended approach to deal with the limit of storage space is to adopt multiple PlexiMail identities (addresses) and associate them with different repositories. It is always a good idea to compartmentalize the exposure of your identities per your application scenarios. It also has the added benefit of additional free Web3 storage allotment, as each of the first 5 GB of free storage is tied to your specific email account (hence restricted to a specific facet of your PII) when it is first applied for. If any of your application scenarios requires more than 5 GB of storage space, you probably need to evaluate your risk of putting all your eggs in one basket.
Within the various lineages of Chrome browser, the best practice for managing your separate PlexiMail Identities is to maintain each identity as a Chrome Profile, each of which actually owns its own sandbox and hence its separate PlexiMail wallet. It is suggested to maintain a single identity per profile, namely a single identity account per wallet. (It gets complicated quickly if you maintain many PlexiMail accounts within the same wallet to establish multiple PlexiMail identities.) A good and popular practice is to maintain multiple identities through multiple configurations each of which has its own configuration Crypton.
TOFU (Trust On First Use)
Trust Establishment
This is the same mechanism as that under Counterseal Secure Email, previously documented here. Each time a PlexiMail party needs to re-register their identity with the smart contract, a new TOFU process must be conducted again. This is to establish the trust between two communicating parties without involving any third-party intermediaries or service providers by authenticating the parties on a personal basis involving the proof of ownership of the matching private keys and their respective end-to-end encrypted session credentials.
We'd like to offer a simple tip on how to confidentially share your PlexiMail public address with friends and partners. Here's the process:
Beside your already configured PlexiMail Address (Pub-1), establish and set up a distinct "burner" address (Pub-b). This secondary address, Pub-b, is solely intended for introducing Pub-1 to individuals whose email addresses you possess. Keep Pub-b as "Unverified," and refrain from registering it with the smart contract.
Compose a pleximail using Pub-b as the sender and your friend's (conventional) email as the recipient. This action triggers the Email Bridging function. In the email content, identify yourself and state your intention to associate yourself with the address Pub-1. Lock the content of this bridged email with a passcode. Reach out to the recipient (through a non-PlexiMail channel or "out-of-band" such as email, text, Whatsapp, Signal, Telegram, etc.) and inform them about this confidential delivery of your PlexiMail address, along with the passcode needed to unlock it. Use a burner email/phone account if deemed necessary.
Your friend will receive an email from aifinoreply@gmail.com containing a clickable button that directs them to the mail.ai-fi.cc website, where they can access your bridged email. The email can only be decrypted by entering the passcode. In the decrypted email, the sender's PlexiMail Address will be displayed as Pub-b, while your true address (Pub-1) will be presented in the email's body.
The exposed metadata in this process includes: 1) The agent aifinoreply@gmail.com being aware that a PlexiMail user attempted to contact the recipient's (conventional) email, with no knowledge about Pub-1. 2) The recipient's email provider knowing that a PlexiMail user made contact without specific details. 3) The "out-of-band" channel observing the passcode, excluding the background story. In other words, no providers, including even the PlexiMail "utility server" aifinoreply@gmail.com, can trace these steps back to Pub-1.
Remember not to use Pub-b for any other purposes unless you have a valid reason to do so. You do need to maintain an additioinal crypton for Pub-b or many if you want to use it as a burner address. There are numerous ways to inform your mail recipient about your PlexiMail address. Modify the degree of strictness based on your individual circumstances.
One-way Confirmation
In scenarios where only one end of the communication is interested in their anonymity, the other end may publish its identity and PlexiMail addresses without treating their addresses as "burners" or private assets. The TOFU verification/confirmation on the party representing a public site simply involves a SSL access to its public site and retrieves their published PlexiMail addresses. This is most common when a merchant wants to offer anonymity when dealing with their privacy-conscious customers. The motivation is similar to Facebook's supporting a Dark Web site.
Double-Check The TOFU Signature Personally
To further guarantee the authenticity of the party on the other end of the TOFU without trusting even the PlexiMail open source and low-level PlexiMail utility services, a user may want to personally verify the signature involved in the TOFU protocol based on the public Ethereum Signature standard. A well-trusted third-party verification tool is as follows:
- Go to https://etherscan.io/verifiedSignatures and Click Verify Signature.
- On the Etherscan Verify Signature pop-up, fill the data fields Address, Message, and Signature Hash with Sender address, Identity Key, Signature respectively embedded within the TOFU message. Data displayed in TOFU messages are all clickable for copy and paste.
A self-conducted signature verification based on non-PlexiMail services makes the TOFU protocol trustless relative to the PlexiMail as the minimalistic service provider.
Standalone Application Option
** Deprecated: This feature is no longer considered to be consistent with the "Traceless" goal of PlexiMail. A dedicated PlexiMail PWA browser configuration displayed on any device reveals the fact that the device owner is a PlexiMail user. **
At the end of the initial setup, users are given the choice of how the PlexiMail is to run: as a web app by visiting https://ai-fi.cc or alternatively as a "standalone" web application (PWA) with its own dedicated window like a native app, which has its own launchable taskbar entry with the ai-fi.cc logo  . When it is pressed to run, it just looks like an ordinary web browser screen with a single default web page presented but not associated with any other browser bookmarks or options.
. When it is pressed to run, it just looks like an ordinary web browser screen with a single default web page presented but not associated with any other browser bookmarks or options.
Cost of PlexiMail
PlexiMail is free in the sense that the PlexiMail Web3 Edition is freely offered. However, certain consumables, such as electricity, computing power, traditional disk storage, RAM, printer, ink, and internet connectivity, are not included. It operates as a sustainable self-service platform, not as a charity. PlexiMail intends to be owned and supported by all of us when we wish to engage with one another outside the realm of Surveillance Capitalism.
This PlexiMail Web3 Edition is a Web3 dApp and sometimes consumes “blockchain gas”, which is the charge by the blockchain for your consumption of its computational resources. There are two transactions that cost gas: Every time you re-register/re-verify to a new blockchain account, it requires the execution of PlexiMail smart contract on the Avalanche blockchain or other supported blockchains, the cost of which fluctuates and currently at less than $1 for Avalanche. If you stick to only one PlexiMail address, this cost is incurred only once at the initiation of a new account. Note that this charge for registering with the smart contract is optional. You can carry out the same smart contract verification task yourself by hand during the TOFU process. Additionally, every time a PlexiMail is sent, we may charge a few AVAX, which is the smallest denomination of AVAX (1 AVAX = 1,000,000,000 nAVAX) and is about a fraction of a penny. This charge is usually to thwart DDOS (Denial of Service) when the situation demands it and is negligible to you if you have left some cryptos in your wallet. This cost is partially to fund the off-chain data, maintained for carrying out the E2EE and other PII hiding schemes.
PlexiMail Smart Contract as an Option
The PlexiMail Smart Contract is defined as the PlexiMail Trustless Identity Registration Service. You may equate it to those SSL/TLS Certificate Authorities, commonly referred as CA's, that store, sign, and issue digital certificates for websites supporting HTTPS, which certify the ownership of a public key by the named subject on the certificate. In the spirit of Web 3.0, PlexiMail takes a step further in eliminating the trust of any service providers (like those CA's) and relying only on the trustless PlexiMail Smart Contract running on Ethereum or other supported blockchains. One of the prominent benefits of registering with the Smart Contract is the "auditability" gained. A registered PlexiMail address can be frequently audited to timely discover any "hijack" event, that conceivably also leaves some digital "exhaust" or "breadcrumb".
Although we consider this concern of "exhaust" or "breadcrumb" misplaced, given the fact that all PlexiMail addresses are self-created, self-managed and truly pseudonymous, we've made the registering with the PlexiMail Trustless Identity Registration Service an option if a user opts to forego the benefit of "auditability" or to save the registration cost, which amounts to around $10 at the time of the first software release for Ethereum and much cheaper for other supported blockchain like Avalanche (less than $1). Without the utility of the Smart Contract for auditability, we'd strongly suggest our users take extra caution when conducting the TOFU (Trust On First Use) protocol in dealing with those contacts whose addresses are not registered or listed with the Smart Contract, frequently marked as "Unverified" by PlexiMail. Security practices are a never-ending tradeoff of what-if decisions.
Traffic Attack Mitigation
As a Web3 dApp striving to disengage from any service providers and eliminate the need for trackable user accounts, PlexiMail defends against most traffic attacks by regulating access through a flexible scheme of service fees. This approach also benefits "Verified" users who have registered with the PlexiMail Smart Contract, completed the authentication/qualification process, and have already incurred and settled the associated fees. Those users are granted priority access to the various PlexiMail facilities, particularly during crunch times when PlexiMail identifies DDNS attacks. Moreover, PlexiMail dynamically initiates charging for its utility services when traffic attack alarms are triggered. During such alarms, users have the option to pay for an urgent service using funds from their wallet or choose to wait until the situation subsides.
Funding the PlexiMail Wallet
For average users not familiar with the crypto ecosystem, the concept of crypto account, wallets and crypto transactions are understandably foreign. They are well advised not to confuse trustlessness of the blockchain with anonymity. Almost all popular cryptocurrencies are neither private nor anonymous. Actually, the opposite is true that individuals' transactions on the blockchain are recorded permanently, immutable, in plain sight and fully traceable. To deal with this unwanted traceability, and also to ease the onboarding process for PlexiMail users that need to spend a small amount of startup cryptos to fund their wallets in order to deal with our Smart Contract, PlexiMail supports a service that would allow our users to purchase a small amount of digital cash in order to register with the PlexiMail Smart Contract through their built-in Ai-Fi wallet with total anonymity.

The process of purchasing unfolds across two distinct steps: the initial acquisition of "digital cash" through established payment methods like credit/debit cards (such as those supported by Stripe), and the subsequent transfer of the secured digital cash to the user's wallets. This digital cash inherently adopts the characteristics of a token voucher, subject to a transformative procedure referred to as "blinding," executed through a blinding passcode. That passcode, which is cryptographically mixed with the payment during the purchase process, remains under the control of the purchaser throughout all stages and remains hidden. In the subsequent phase, the exclusive authority to "unblind" the voucher rests solely with the purchaser, enabling anonymous redemption or expenditure of the voucher. This entire process serves to finance a crypto account with absolute untraceability, akin to physical cash.Please go to the "Tokens" tab on our main webpage here to learn more.
Background
This document introduces a Counterseal Web3 dApp, a web-based email application accessible by visiting https://ai-fi.cc. Due to the repidly evolving feature set under the breakneck speed of the Web 3.0, we'd like to suggest you to first peruse the Release Notes at the end of this write-up ahead of your reading it. Many features have been deprecated and/or improved as we inch toward our first release.
In this part of the Help texts we've gone through the background info minimally required before participating in the PlexiMail framework, the understanding of which would help you set up the configuration to support its operations. Before the configuration setup, please first complete the preparation steps outlined Configuration Setup, which will be used to create a configuration file for our dApp when you are accessing our website the first time.
The main focus of this dApp is to extend the original function set of PlexiMail offered under the Counterseal framework, which is an overlay above the traditional federated email infrastructure for supporting Signal-based end-to-end encryption and therefore not able to protect the Metadata. This new Web3-based email implementation retains the original end-to-end privacy protection as PlexiMail, but fundamentally shifts our approach in Metadata cloaking.
We refer to this version of Counterseal email as PlexiMail, considering its advanced Web3 architecture afforded to us by the recent availability of the vast amount of cloud storage space, an offering spearheaded primarily by Filecoin, touted as "a decentralized storage network for humanity's most important information". Practically overnight, we are liberated from the chokehold of service providers by owning our own almost infinite amount of network storage, to all practical purposes, for communicating with our family, friends and business partners. Coupled with the ample bandwidth that we, as individuals, have already paid for in connecting to the Internet, we can now reclaim our email communication and thwart any unwanted surveillance on both our data and metadata at the same time.
Before we smooth out all the rough edges of our latest release, our users need to carry out a few more steps necessary in setting this package up than what they are accustomed to, as the handholding of a traditional email service provider is no longer there to assist them in order to earn your patronage. Current release assumes that our early adopters care greatly about their privacy and are willing to go the extra mile to protect it. Needless to say, there is an extra step for acquiring web3 storage from Filecoin (currently) so that E2EE (End2End Encryption) can be conducted without leaking metadata. (Traditional service-provider-based email architecture is actually an e-postcard, with both the content, sender and all recipients in the clear.) Although the risk of phishing attacks is low, we take advantage of the Smart Contract on supported blockchains to effectively block both the phishing attacks and DDOS (Distributed Denial of Service) in one fell swoop. It also allows individual users to audit whether their identities have been meddled with or even hijacked.
Release Notes
The inclusion of support for MetaMask and other crypto wallets in PlexiMail was initially motivated by their popularity and convenience during the early development phase. However, we have deprecated their support to minimize the traceability of your PlexiMail addresses. Instead, we offer a built-in custom wallet for the express purpose of supporting PlexiMail. This built-in PlexiMail wallet focuses solely on fulfilling the requirements specific to PlexiMail, which greatly simplifies our reliance on blockchain transactions. As always, simplicity improves security and makes privacy issues transparent.
The support for the Ethereum blockchain and its Testnet Sepolia/Goerli is no longer available due to performance issues and their high service charges. We have now adopted the Avalanche blockchain for smart contract support, which offers more reasonable transaction charges. We also encourage you to utilize our Plexi Token Service as a digital cash store for anonymously refilling your wallet. Although it requires two separate steps to fund your AVAX wallet, it accepts credit cards and allows you to convert purchased tokens into digital cash to anonymously pay for registering your digital identities on the Avalanche blockchain.
Web3Storage is highly advanced and offers huge potential in our effort in reclaiming the Internet service infrastructure in terms of privacy and independence. However, utilizing our own cloud storage space for storing our private messages without relying on mediating service providers has some teething problems, among which the occasional performance penalty is one. The upload/download operations are quite reliable, albeit with some delays occasionally. Some patience is called for.
Support for multiple PlexiMail identities or accounts managed by a single control mechanism is of high priority to our future development. This implies extending our Counterseal CryptoWallet for PlexiMail, with the added Threshold Signature support. Additional CryptoWallet support will make the startup more friendly and the Threshold Signature will provide hardware redundancy for even stronger security factors. The CryptoWallet and all mobile components will be integrated into the Authenticator on various mobile platforms.